What is metadata and should we be concerned about it?
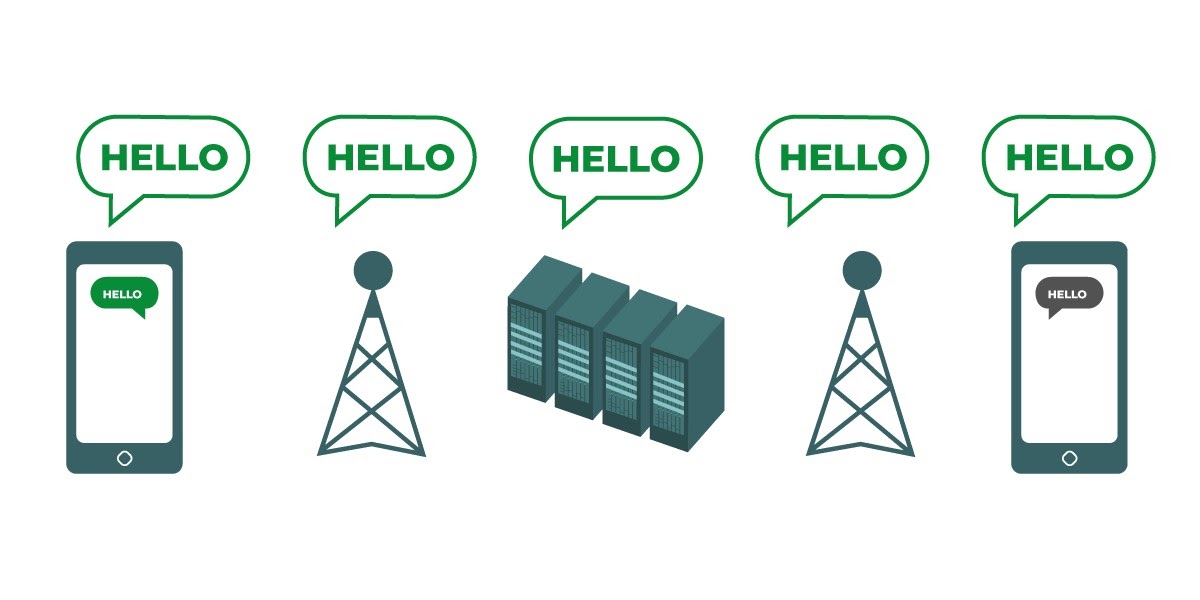
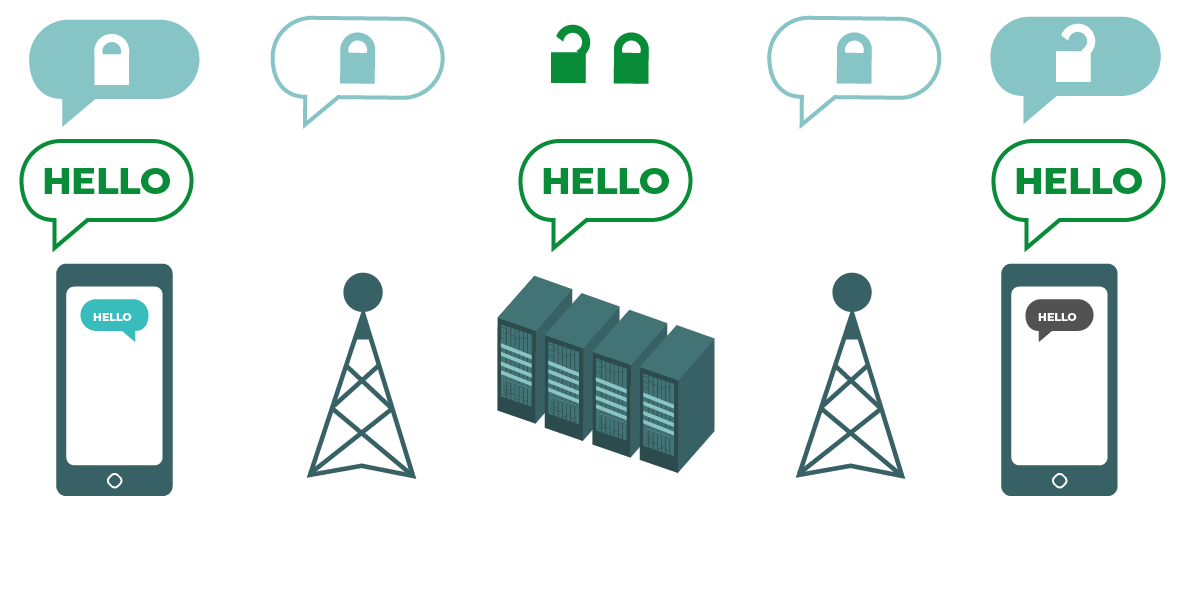
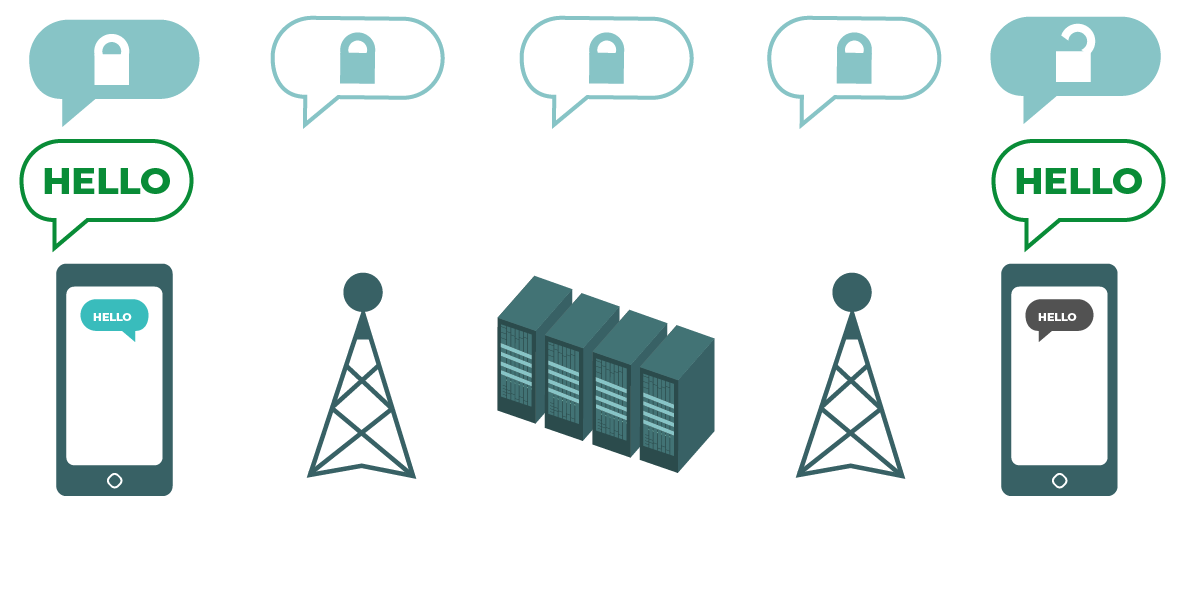
Who you and your staff talk to and when and where you talk to them can often be just as sensitive as what you talk about. It is important to remember that end-to-end encryption only protects the contents (the “what”) of your communications. This is where metadata comes into play. EFF’s Surveillance Self-Defense Guide provides an overview of metadata and why it matters to organizations (including an illustration of what metadata looks like):
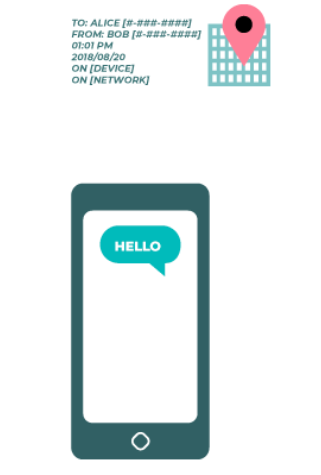
Metadata is often described as everything except the content of your communications. You can think of metadata as the digital equivalent of an envelope. Just like an envelope contains information about the sender, receiver, and destination of a message, so does metadata. Metadata is information about the digital communications you send and receive. Some examples of metadata include:
- who you are communicating with
- the subject line of your emails
- the length of your conversations
- the time at which a conversation took place
- your location when communicating
Even a tiny sample of metadata can provide an intimate lens into your organization’s activities. Let us take a look at how revealing metadata can actually be to the hackers, government agencies, and companies that collect it:
- They know you called a journalist and spoke with them for an hour before that journalist published a story with an anonymous quote. However, they do not know what you talked about.
- They know one of your party candidates frequently messaged a local business infamous for unsavory activity. But the topic of the messages remains a secret.
- They know you got an email from a COVID testing service, then called your doctor, then visited the World Health Organization’s website in the same hour. However, they do not know what was in the email or what you talked about on the phone.
- They know you received an email from a large donor with the subject line “Return on Our Investment After the Election”. But the content of the email is invisible to them.
Metadata is not protected by the encryption provided by most message services. If you are sending a message on WhatsApp, for example, keep in mind that while the contents of your message are end-to-end encrypted, it is still possible for others to know who you are messaging, how frequently, and, with phone calls, for how long. As a result, you should keep in mind what risks exist (if any) if certain adversaries are able to find out who your organization talks to, when you talked to them, and (in the case of email) the general subject lines of your organization’s communications.
One of the reasons that Signal is so highly recommended is that, in addition to providing end-to-end encryption, it has introduced features and made commitments to reduce the amount of metadata that it records and stores. For instance, Signal’s Sealed Sender feature encrypts the metadata about who is talking to whom, so that Signal only knows the recipient of a message but not the sender. By default this feature only works when communicating with existing contacts or profiles (people) with whom you have already communicated or whom you have stored in your contacts list. However you can enable this “Sealed Sender” setting to “Allow from anyone” if it is important for you to eliminate such metadata across all Signal conversations, even those with people unknown to you.
What about email?
Most email providers, for example Gmail, Microsoft Outlook, and Yahoo Mail, employ transport-layer encryption. So if you must communicate sensitive content using email and are worried that your email provider could be legally required to provide information about your communications to a government or another adversary, you may want to consider using an end-to-end encrypted email option. Keep in mind, however, that even end-to-end encrypted email options leave something to be desired from a security perspective, for example, not encrypting subject lines of emails and not protecting metadata. If you need to communicate particularly sensitive information, email is not the best option. Instead opt for secure messaging options like Signal.
If your organization does continue to use email, it is critical to adopt an organization-wide system. This helps you limit the common risks that arise when staff use personal email addresses for their work, such as poor account security practices. For example, by providing organization-issued email accounts to staff, you can enforce best practices like strong passwords and 2FA on any accounts your organization manages. If, according to your analysis above, end-to-end encryption is necessary for your email, both Protonmail and Tutanota offer plans for organizations. If transport-layer encryption is adequate for your organization’s email, options like Google Workspace (Gmail) or Microsoft 365 (Outlook) can be useful.
Can we really trust WhatsApp?
WhatsApp is a popular choice for secure messaging, and can be a good option given its ubiquity. Some people are concerned that it is owned and controlled by Facebook, which has been working to integrate it with its other systems. People are also concerned about the amount of metadata (i.e. information about with whom you communicate and when) that WhatsApp collects. If you choose to use WhatsApp as a secure messaging option, be sure to read the above section on metadata. There are also a few settings that you need to ensure are properly configured. Most critically, be sure to turn off cloud backups or, at the very least, enable WhatsApp’s new end-to-end encrypted backups feature using a 64 digit encryption key or long, random, and unique passcode saved in a secure place (like your password manager). Also be sure to show security notifications and verify security codes. You can find simple how-to guides for configuring these settings for Android phones here and iPhones here. If your staff *and those with whom you all communicate* do not properly configure these options, then you should not consider WhatsApp to be a good option for sensitive communications that require end-to-end encryption. Signal still remains the best option for such end-to-end encrypted messaging needs given its secure default settings and protection of metadata.
What about texting?
Basic text messages are highly insecure (standard SMS is effectively unencrypted), and should be avoided for anything that is not meant for public knowledge. While Apple’s iPhone-to-iPhone messages (known as iMessages) are end-to-end encrypted, if a non-iPhone is in the conversation the messages are not secured. It is best to be safe and avoid text messages for anything remotely sensitive, private, or confidential.
Why aren’t Telegram, Facebook Messenger, or Viber recommended for secure chats?
Some services, like Facebook Messenger and Telegram, only offer end-to-end encryption if you deliberately turn it on (and only for one-to-one chats), so they are not good options for sensitive or private messaging, especially for an organization. Do not rely on these tools if you need to use end-to-end encryption, because it is quite easy to forget to change away from the default, less secure settings. Viber claims to offer end-to-end encryption, but has not made its code available for review to outside security researchers. Telegram’s code has also not been made available for a public audit. As a result, many experts fear that Viber’s encryption (or Telegram’s “secret chats”) may be substandard and therefore not suitable for communications that require true end-to-end encryption.
Our contacts and colleagues are using other messaging apps - how can we convince them to download a new app to communicate with us?
Sometimes there is a tradeoff between security and convenience, but a little extra effort is worth it for sensitive communications. Set a good example for your contacts. If you have to use other less secure systems, be very conscious of what you are saying. Avoid discussion of sensitive topics. For some organizations, they may use one system for general chatting and another with leadership for the most confidential discussions. Of course, it is simplest if everything is just automatically encrypted all the time - nothing to remember or think about.
Luckily, end-to-end encrypted apps like Signal are becoming increasingly popular and user-friendly - not to mention that they have been localized in dozens of languages for global use. If your partners or other contacts need help switching communications over to an end-to-end encrypted option like Signal, take some time to talk them through why it is so important to properly protect your communications. When everyone understands the importance, the few minutes required to download a new app and the couple of days it might take to get used to using it will not seem like a big deal.
Are there other settings for end-to-end encrypted apps that we should be aware of?
In the Signal app, verifying security codes (which they refer to as Safety Numbers) is also important. To view a safety number and verify it in Signal, you can open up your chat with a contact, tap their name at the top of your screen, and scroll down to tap “View Safety Number.” If your safety number matches with your contact, you can mark them as “verified” from that same screen. It is especially important to pay attention to these safety numbers and to verify your contacts if you receive a notification in a chat that your safety number with a given contact has changed. If you or other staff need help configuring these settings, Signal itself provides helpful instructions.
If using Signal, which is widely considered to be the best user-friendly option for secure messaging and one-to-one calls, be sure to set a strong pin. Use at least six digits, and not something easy-to-guess like your birth date.
For more tips on how to properly configure Signal and WhatsApp, you can check out the tool guides for both developed by EFF in their Surveillance Self-Defense Guide.