How can we identify phishing?
Phishing can sound sinister and impossible to catch, but there are some simple steps that everyone in your organization can take to protect against the majority of attacks. The following phishing defense tips are modified and extended from the in-depth phishing guide developed by the Freedom of the Press Foundation, and should be shared with your organization (and other contacts) and integrated into your security plan:
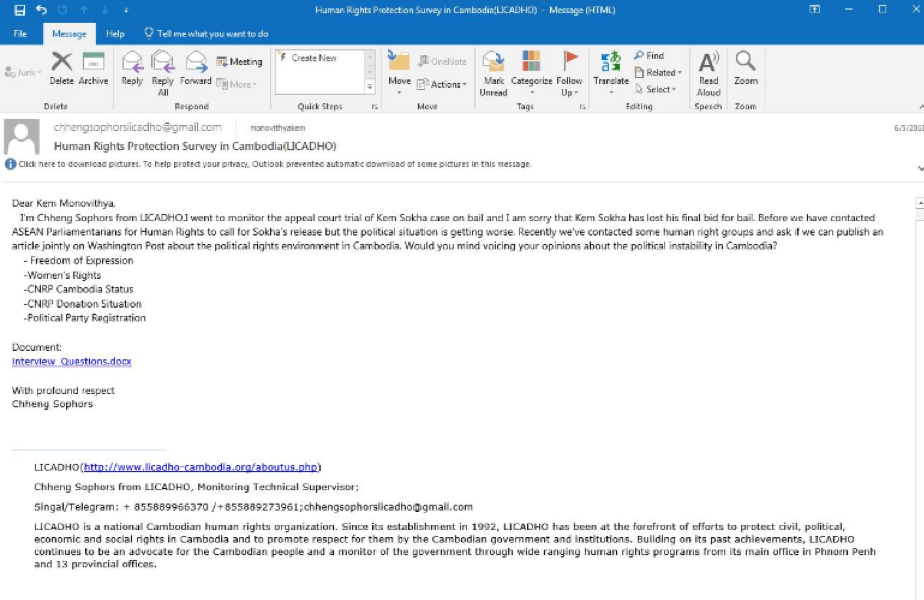
Sometimes, the "from" field is lying to you
Be aware that the "from" field in your emails can be faked or forged to trick you. It is common for phishers to set up an email address that looks a lot like a legitimate one that you are familiar with, misspelled just a bit to trick you. For example, you may receive an email from someone with the address “[email protected]" as opposed to “[email protected]”. Notice the extra Os in google. You may also know someone with an email address “[email protected]”, but receive a phishing email from an impersonator who set up “[email protected]” - the only difference being a subtle change of letters at the end. Always be sure to double-check that you know the sending address of an email before proceeding. A similar concept applies to phishing via text, calls, or messaging apps. If you get a message from an unknown number, think twice before responding to or interacting with the message.
Beware of attachments
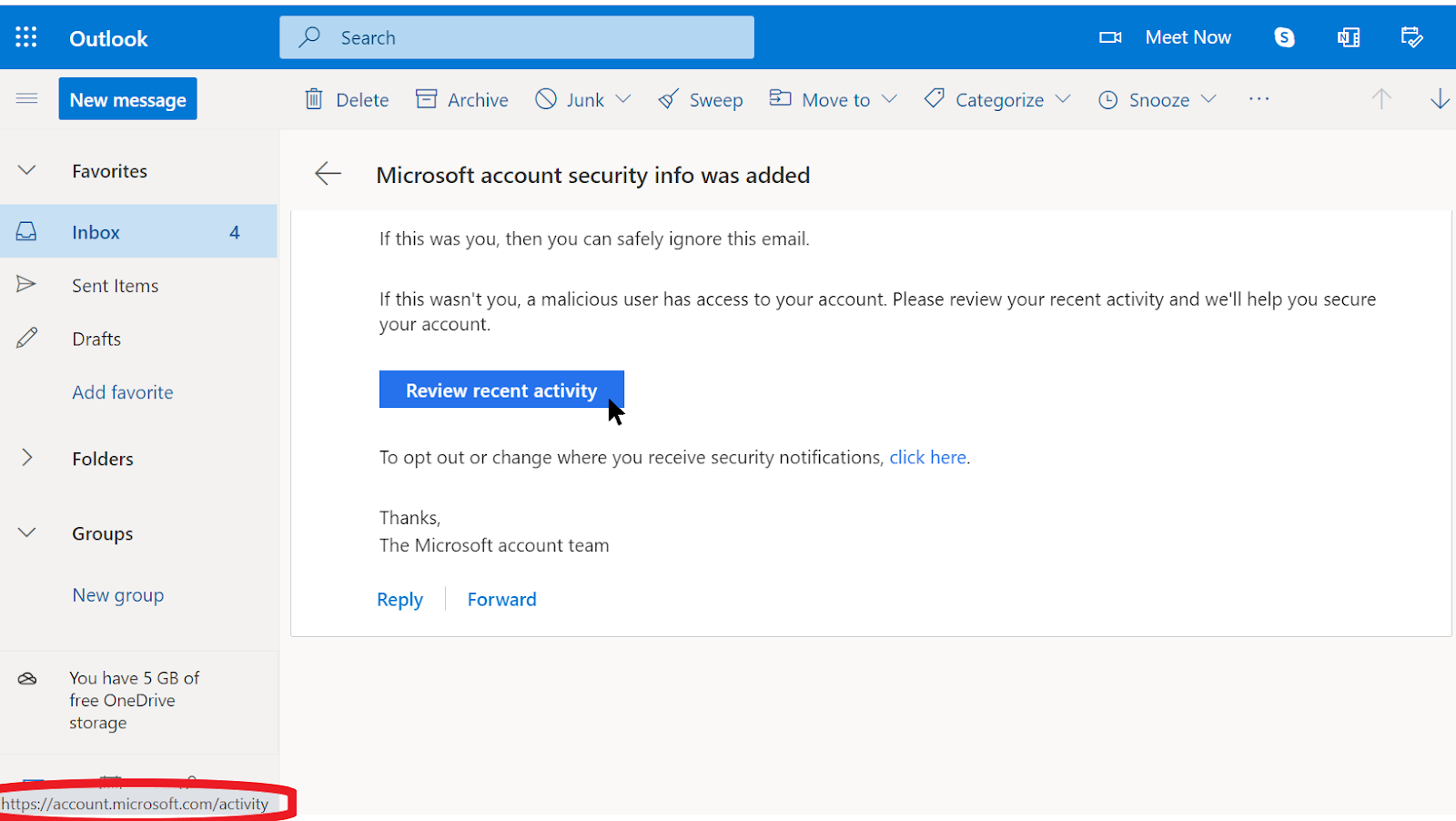
Attachments can carry malware and viruses, and commonly accompany phishing emails. The best way to avoid malware from attachments is to never download them. As a rule, do not open any attachments immediately, especially if they come from people you do not know. If possible, ask the person that sent you the document to copy-paste the text in an email or to share the document via a service like Google Drive or Microsoft OneDrive, which have built-in virus scanning of most documents uploaded to their platforms. Build an organizational culture where attachments are discouraged.
If you absolutely have to open the attachment, it should only be opened in a safe environment (see Advanced section below) where potential malware cannot be deployed to your device.
If you use Gmail and receive an attachment in an email, instead of downloading it and opening it on your computer, simply click on the attached file and read it in “preview” within your browser. This step allows you to view the text and contents of a file without downloading it or allowing it to load possible malware onto your computer. This works well for word documents, PDFs, and even slideshow presentations. If you need to edit the document, consider opening the file in a cloud program like Google Drive and converting the file to a Google Doc or Google Slides.
If you use Outlook, you can similarly preview attachments without downloading them from the Outlook web client. If you need to edit the attachment, consider opening it in OneDrive if that’s available to you. If you use Yahoo Mail, the same concept applies. Do not download attachments, but rather preview them from within the web browser. Regardless of what tools you have at your disposal, the best approach is simply to never download attachments that you do not know or trust, and regardless of how important an attachment might seem, never open something with a file type you do not recognize or have no intention of ever using.