Last Updated: July 2022
Using HTTPS
The most important step to limiting an adversary’s ability to surveil your organization online is to minimize the amount of information available about you and your colleagues’ internet activity. Always make sure you are connecting to websites securely: make sure the URL (location) starts with “https'' and shows a small lock icon in the address bar of your browser.
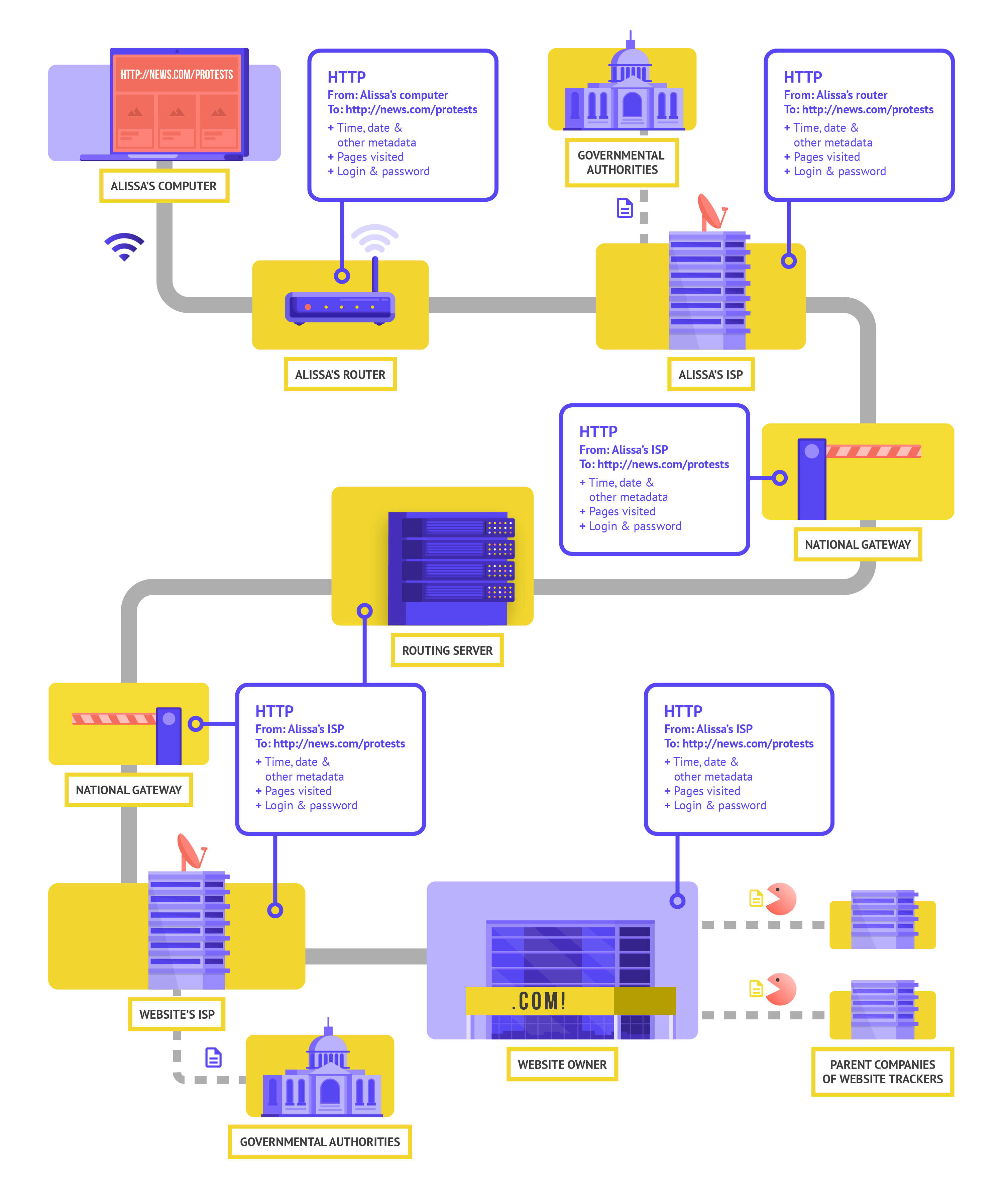
When you browse the internet without encryption, the information you type into a site (like passwords, account numbers, or messages), and the details of the site and pages you are visiting are all exposed. This means that (1) any hackers on your network, (2) your network administrator, (3) your ISP and any entity they might share data with (like governmental authorities), (4) the ISP of the site you are visiting and any entity they might share data with, and of course (5) the site you are visiting itself all have access to quite a bit of potentially sensitive information.
Let’s take a real-world example of what browsing without encryption looks like:
When browsing without encryption, all of your data is exposed. This includes where you are, the sites and pages you visit, and your passwords and other sensitive data that you type into a log-in page, form, or the website itself. As shown above, an adversary can see where you are, that you are going to news.com, looking specifically at the page on protests in your country, and see your password that you share to log in to the site itself. Such information in the wrong hands not only exposes your account but also gives potential adversaries a good idea of what you might be doing or thinking about.
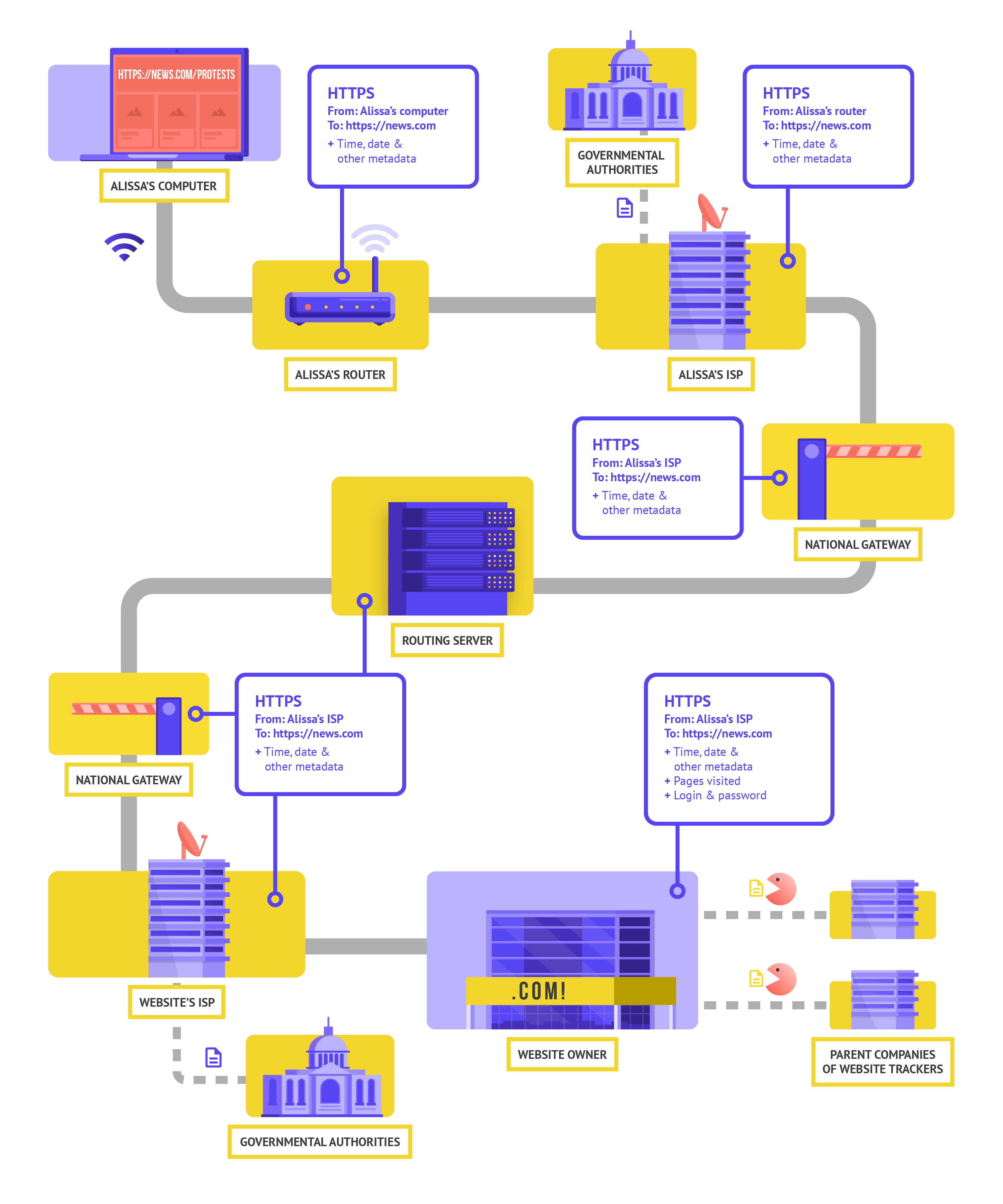
Using HTTPS (the “s” stands for secure) means that encryption is in place. This offers you much more protection. Let’s take a look at what browsing with HTTPS (aka with encryption) looks like:
When browsing with HTTPS in place on a site, the information that you share to a website is encrypted. However, people can still see where you are and what sites you visit. Sophisticated adversaries can also see the specific pages you go to on a given site. With HTTPS in place, a potential adversary can no longer see your password or other sensitive information that you might share to a website. They can, however, still see what domains (for example, news.com) you are visiting. And while HTTPS also encrypts information about the individual pages within a site (for example, website.com/protests) that you visit, sophisticated adversaries can still see this information by inspecting your internet traffic. With HTTPS in place, an adversary might know that you are going to news.com, but they would not be able to see your password, and it would be more difficult (but not impossible) for them to see that you are looking up information about protests (to use this one example). That is an important difference. Always check that HTTPS is in place before navigating through a website or entering sensitive information. You can also use the HTTPS Everywhere browser extension to ensure you are using HTTPS at all times, or if you use Firefox, turn on HTTPS only mode in the browser.
If you are presented with a warning from your browser that a website might be insecure, do not ignore it. Something is wrong. It might be benign – like the site has an expired security certificate – or the site might be maliciously spoofed or faked. Either way, it is important to heed the warning and not proceed to the site.
Using Encrypted DNS
If you want to make it more difficult (but not impossible) for an ISP to know the details of the websites that you visit, you can use encrypted DNS.
If you are wondering, DNS stands for Domain Name System. It is essentially the phonebook of the internet, translating human-friendly domain names (like ndi.org) to web-friendly internet protocol (IP) addresses. This allows people to use web browsers to easily look up and load internet resources and visit websites. By default though, DNS is not encrypted.
To use encrypted DNS and add a bit of protection to your internet traffic at the same time, one easy option is to download and turn on Cloudflare’s 1.1.1.1 app on your computer and mobile device. Other encrypted DNS options, including Google’s 8.8.8.8, are available but require more technical steps to configure. If you use Firefox browser, encrypted DNS is now turned on by default. Users of Chrome or Edge browsers can turn on encrypted DNS through the browser’s advanced security settings by turning on “use secure DNS” and selecting “With: Cloudflare (1.1.1.1)” or the provider of their choice.
Cloudflare’s 1.1.1.1 with WARP encrypts your DNS and encrypts your browsing data - providing a service similar to a traditional VPN. While WARP does not fully protect your location from all websites that you visit, it is an easy-to-use feature that can help your organization’s staff take advantage of encrypted DNS and additional protection from your ISP in situations where a full VPN is either not functional or required given the threat context. In the 1.1.1.1 with WARP advanced DNS settings, staff can also turn on 1.1.1.1 for Families to provide additional protection against malware while accessing the internet.
HTTPS is essential and encrypted DNS provides some extra protection against snooping and site blocking, but if your organization is concerned about highly targeted surveillance regarding your online activities and faces sophisticated censorship online (such as websites and apps being blocked), you might want to use a trusted virtual private network (VPN).
What is a VPN?
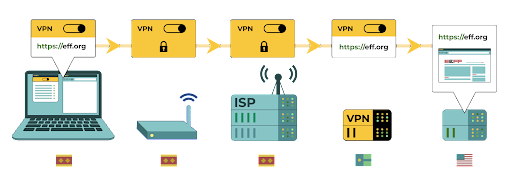
A VPN is essentially a tunnel that protects against the surveillance and blocking of your internet traffic from hackers on your network, your network administrator, your ISP, and anyone they might share data with. It is still essential to use HTTPS and to ensure that you trust the VPN that your organization uses. Here is an example of what browsing with a VPN looks like:
To describe VPNs in more depth, this section references EFF’s Surveillance Self-Defense Guide:
Traditional VPNs are designed to disguise your actual network IP address and create an encrypted tunnel for the internet traffic between your computer (or phone or any networked “smart” device) and the VPN’s server. Because traffic in the tunnel is encrypted and sent to your VPN, it is much harder for third parties like ISPs or hackers on public Wi-Fi to monitor, modify, or block your traffic. After going through the tunnel from you to the VPN, your traffic then leaves the VPN to its ultimate destination, masking your original IP address. This helps to disguise your physical location for anyone looking at traffic after it leaves the VPN. This offers you more privacy and security, but using a VPN does not make you completely anonymous online: your traffic is still visible to the operator of the VPN. Your ISP will also know that you are using a VPN, which might raise your risk profile.
This means that choosing a trustworthy VPN provider is essential. In some places like Iran, hostile governments have actually set up their own VPNs to be able to track what citizens are doing. To find the VPN that is right for your organization and its staff, you can evaluate VPNs based on their business model and reputation, what data they do or do not collect, and of course the security of the tool itself.
Why should you not just use a free VPN? The short answer is that most free VPNs, including those that come pre-installed on some smartphones, come with a big catch. Like all businesses and service providers, VPNs have to sustain themselves somehow. If the VPN does not sell its service, how is it keeping its business afloat? Does it solicit donations? Does it charge for premium services? Is it supported by charitable organizations or funders? Unfortunately, many free VPNs make their money by collecting and then selling your data.
A VPN provider that does not collect data in the first place is the best choice. If the data is not collected, it cannot be sold or handed over to a government if requested. When looking through a VPN provider’s privacy policy, see whether the VPN actually collects user data. If it does not explicitly state that user connection data is not being logged, chances are that it is. Even if a company claims not to log connection data, this may not always be a guarantee of good behavior.
It is worthwhile to do a search on the company behind the VPN. Is it endorsed by independent security professionals? Does the VPN have news articles written about it? Has it ever been caught misleading or lying to its customers? If the VPN was established by people known in the information security community, it is more likely to be trustworthy. Be skeptical of a VPN offering a service that no one wants to stake their reputation on, or one that is run by a company that no one knows about.
So what VPN should we use?
If using a VPN makes sense for your organization, a couple of trustworthy options include TunnelBear and ProtonVPN. Another option is to configure your own server using Jigsaw’s Outline, where there is not a company managing your account, but in return you have to set up your own server. If your organization is a bit larger, you may want to consider a business VPN that provides account management features such as TunnelBear’s Teams plan.
Although most modern VPNs have improved in regard to performance and speed, it is worth keeping in mind that using a VPN might slow down your browsing speed if you are on a very low-bandwidth network, suffer from high latency or network delays, or experience intermittent internet outages. If you are on a faster network, you should default to using a VPN all the time.
If you do recommend that staff use a VPN, it is also important to ensure that people keep the VPN turned on. It might sound obvious, but a VPN that is installed but not running does not provide any protection.
Anonymity through Tor
In addition to VPNs, you may have heard of Tor as another tool for more securely using the internet. It is important to understand what both are, why you might use one or the other, and how both might impact your organization.
Tor is a protocol for transmitting data anonymously over the internet by routing messages or data through a decentralized network. You can learn more about how Tor works here, but in short, it routes your traffic through multiple points along the way to its destination so that no single point has enough information to expose who you are and what you are doing online at once.
Tor is different from a VPN in a few ways. Most fundamentally, it differs because it does not rely on trust of any one specific point (like a VPN provider).
This graphic, developed by EFF, shows the difference between a traditional VPN and Tor.
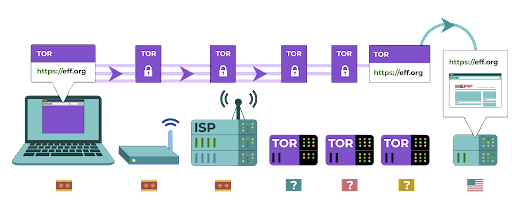
The easiest way to use Tor is through the Tor web browser. It operates like any normal browser except that it routes your traffic through the Tor network. You can download the Tor browser on Windows, Mac, Linux or Android devices. Keep in mind that when using Tor Browser, you are only protecting the information you access while in the browser. It does not provide any protection to other apps or downloaded files that you might open separately on your device. Also keep in mind that Tor does not encrypt your traffic, so - much like when using a VPN - it is still essential to use best practices like HTTPS when browsing.
If you would like to extend the anonymity protections of Tor to your entire computer, more tech savvy users can install Tor as a systemwide internet connection, or consider using the Tails operating system, which routes all traffic through Tor by default. Android users can also use the Orbot app to run Tor for all internet traffic and apps on their device. Regardless of how you use Tor, it is important to know that when using it, your internet service provider cannot see what websites you are visiting but they *can* see that you are using Tor itself. Much like when using a VPN, this could raise the risk profile of your organization considerably, because Tor is not a very common tool and therefore stands out to adversaries that may be monitoring your internet traffic.
So, should your organization use Tor? The answer: it depends. For most at-risk organizations a trusted VPN that is properly used by all staff at all times is easiest, most convenient, and in the age of greater VPN usage globally, less likely to raise red flags. However if you either cannot afford a trustworthy VPN or operate in an environment where VPNs are routinely blocked, Tor can be a good option, if legal, for limiting the impact of surveillance and avoiding censorship online.
Are there any reasons we should not use a VPN or Tor?
Apart from concerns around non-reputable VPN services, it is important to be aware whether using a VPN or Tor is legal in your country. If such tools are illegal where your party operates, or if the use of these tools might cause more attention or risk than simply navigating the web with standard HTTPS and encrypted DNS, then a VPN or Tor would not be the right choice. Although your ISP will not know what sites you are visiting while using these services, they can see that you are connected to Tor or a VPN. However, defaulting to having a trustworthy VPN on all the time is the best choice for most political parties if legal and possible.
What browser should we be using?
Use a reputable browser such as Chrome, Firefox, Brave, Safari, Edge, or Tor Browser. Both Chrome and Firefox are very widely used and do a great job with security. Some people prefer Firefox given its privacy focus. Either way, it is important that you restart them and your computer relatively frequently to keep your browser up to date. If you are interested in comparing browser features, check out this resource from the Freedom of the Press Foundation.
Regardless of browser, it is also a good idea to use an extension or add-on like Privacy Badger, uBlock Origin, or DuckDuckGo’s Privacy Essentials that stops advertisers and other third-party trackers from tracking where you go and what sites you visit. And when browsing the internet, consider switching your default web searches away from Google to DuckDuckGo, Startpage, or another privacy-protecting search engine. Such a switch will help limit advertisers and third-party trackers as well.

Tibetan political actors were targeted in early 2021 with a cleverly designed malicious browser add-on that stole their email and browsing data. The add-on, which was titled “Flash update components”, was presented to users who visited websites that were linked to phishing emails. Such browser extension or add-on attacks can be just as damaging as malware shared directly through phishing downloads or other software.

.jpg)